
The Wattle Business Services Office is pretty lax when it comes to privacy. They use the same password, Wattle123 for all their IT systems. That way, Business Owner Brad will never forget what it is.
Their endpoint management is pretty much non-existent. Melissa is keen to use her phone for whatever she can, but it isn’t covered under the company’s cybersecurity management system.
Customer information is mainly kept in hardcopy, but it isn’t locked away; Melissa puts it in the filing cabinet along with employee information (and Isaac has already taken a peek at what the other team members are being paid).
And they definitely don’t have a privacy policy – they are only a small team after all.
Any of this sound familiar? If reading this is setting off alarm bells, then it is time to make privacy a priority in your workplace. With the average cost of cybercrime around $276,000 for Australian businesses, you can’t afford to be like Wattle.
Why Privacy Matters
Your organisation has a legal obligation to protect the information they collect, but more than that, your customers and the general public expect it. The COVID-19 app rollout demonstrated the level of public concern over what personal information is collected and how organisations are using it.
As businesses continue to transform digitally, there is a natural growth in the data collected and leveraged to offer improved customer service. But how is that data protected? Do your customers know what you are collecting and how you are using the information? And is it deleted when no longer required?
Strong privacy governance is crucial to building trust with your customer and employees, improving productivity, and developing more efficient processes. It will reduce the risk of a privacy breach and help you to identify and respond rapidly if a breach occurs.
Privacy Awareness Week
This week is Privacy Awareness Week, and we’ve got our top five tips to help you up the ante on your workplace security systems.
1. Implement a Privacy Management Plan
The Office of the Australian Information Commissioner (OAIC) has very helpfully put together a four-step framework to get you on track. Even if your team is only a small one, like Wattle Business Services, you still need to think about your team and your customer’s privacy.
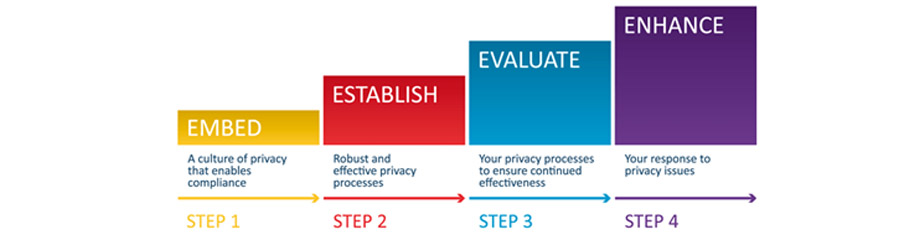
You can download a form to help you establish this framework within your organisation here. https://www.oaic.gov.au/assets/privacy/guidance-and-advice/privacy-management-plan-template-editable.pdf
2. Staff Training
Brad tends to follow the path of least resistance, so he hasn’t pulled Melissa up about using her phone to access work systems. And besides, it is a cost-saving measure if the company doesn’t need to buy her a smartphone, right?
Wrong. It could cost far more than the cost of a smartphone to deal with a system breach – not just in responding to the breach but in lack of trust and potential loss of business.
You need to teach new staff members about your privacy processes as part of their onboarding process and run regular secure information handling sessions to discuss the collection of information, storage, use and disclosure, and deletion.
3. Reduce the risk of a human error data breach
Human error accounts for around 34% of data breaches – you have probably been guilty of one of these yourself. Have you ever sent a large group email and forgotten to BCC the recipients? What about sending a quote or invoice to the wrong person? Maybe you once left your work laptop on the train or lost a file with some paperwork that contained confidential or personal information.
We all make mistakes, but you can minimise the chance of human error data breaches by putting controls in place and educating your staff. For example, setting up a pop-up window that asks for staff confirmation before sending an external email or putting in place a strict policy about taking paperwork off-site.
4. Protect Personal Information
Your staff and your customers deserve to have their privacy protected, both online and in the office itself. This means that electronic HR documentation can’t be saved in public digital folders and physical paperwork should be kept in a locked filing cabinet.
Implementing multi-factor authentication means that you have an additional layer of security to ensure that only the right people are accessing personal information. This means that even if someone was impersonating Brad to try and gain access, they’d have to verify that they really are Brad to access the accounts.
5. Prepare a data breach response plan
This is one of the occasions where ‘it won’t happen to me’ isn’t a plan. We’ve seen businesses here in our local Orange community impacted by ransomware and/or an unintended data breach. As we highlighted earlier, a data breach can be something as simple as Melissa (the millennial receptionist) accidentally sending out the client spreadsheet to the wrong person.
Think about the impact on your business if you were hit by a ransomware attack. How long would your business survive without access to any information or systems? A data breach plan needs to be part of your business continuity strategy.
What needs to be included in your data breach plan? It should follow the four steps of; contain, assess, notify and review.
Guidelines on what to consider can be found here: https://www.oaic.gov.au/privacy/guidance-and-advice/data-breach-preparation-and-response/part-2-preparing-a-data-breach-response-plan/
These are only a few steps you should be taking to #makeprivacyapriority. Privacy Awareness Week brings to the fore many of the considerations you need for your business continuity plan.
We’ll continue to tell the story of Wattle Business Services over the next few months. To see more resources for creating your business continuity plan, visit our business continuity hub here

