
Nope, that wasn’t a typo. Lots of people have decided that lockdown is prime time for a new hobby and rather than catching a few fresh barra for dinner, they are turning to the dark side and engaging in phishing attacks.
Google registered a 20% rise in phishing in 2020, coinciding with a spike in the number of people working from home, often without comprehensive end-point security.
What is phishing?
Phishing involves pretending to be someone else, to convince the victim to give you their personal information or information of value. The most frequent way this occurs is email phishing. We all know not to send our bank details to our long-lost relative who happens to be a prince in Saudi Arabia but what about when you get an email from your boss?
Here is an example that landed in one of our team’s inbox recently:
Good morning,
Hope you don’t have a lot of work to do? Well in case you do, peg it now because i have a task for you to carry out urgently. Drop your number so i can brief you about it all.
Thanks
Mitchell Colton.
Sent from iphone
The email address looked legit, and if the employee had fallen for the scam, the phisher could have used a private number or caller ID spoofing to make it appear that they were the CEO. Luckily, everyone at Colton knows that Mitch would never sign off as Mitchell, and so the jig was up pretty quickly.
Here are a few more examples so that you know what to look out for.
Case Study #1
In between juggling her husband, her two kids and the household on top of keeping Business Owner Brad in line, Office Manager Maggie has been finding working from home a real pain in the back end. When she got an email from Brad asking her to purchase a handful of Westfields vouchers and send through the codes, she did it without a second thought. Unfortunately, it turned out to be a scam. While it didn’t cost the company a huge amount of money, Financial Controller Frank wasn’t happy, and Maggie was pretty shaken up by the whole experience.
While we have used our imaginary friends over at Wattle to demonstrate this case study, this scenario happened to a client several years ago. The employee who was targeted worked in a different office, making the whole scam easier to pull off.
Case Study #2
Financial Controller Frank received an email with a link to a pay an outstanding invoice. At first glance, he thought it might be genuine, as Wattle did use XYZ IT Services when purchasing new printer cartridges. However, there were a few telltale signs that this wasn’t a legitimate business email:
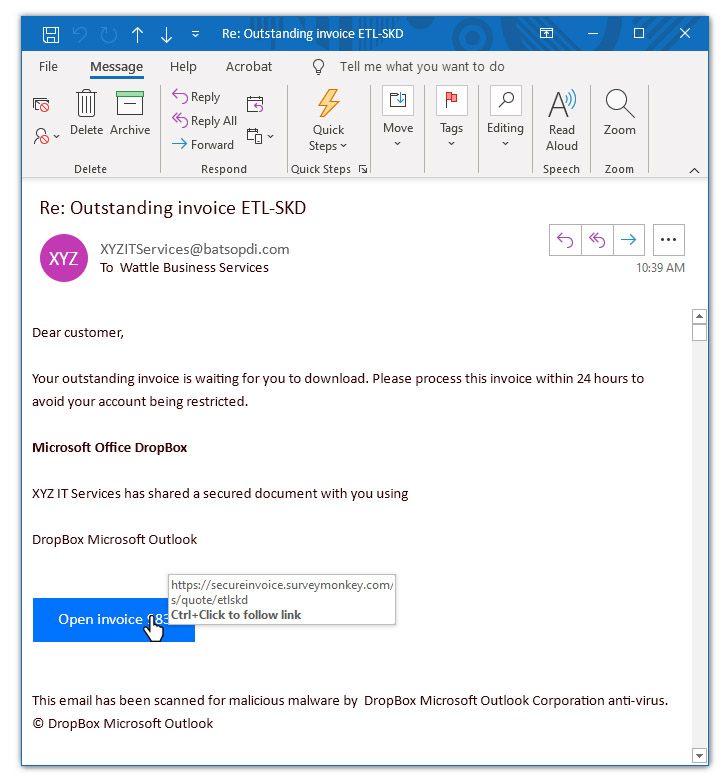
- Firstly, it wasn’t standard business practice for XYZ IT Services to invoice them in this way
- The email isn’t personalised – it is addressed to “customer” rather than to Frank
- There is a mismatch between the subject line of the email and the content – the subject line says “Invoice ETL-SKD” and the download button says “Invoice 983”
- The email refers to Microsoft Office Dropbox, but there is no such thing. Microsoft Office is a suite of desktop productivity applications and Dropbox is an online file hosting service. Microsoft and Dropbox aren’t even part of the same company.
- When you hovered over the link, it redirected to surveymonkey.com and not Microsoft Office Dropbox. This kind of mismatch is a big hint that something is a bit fishy (or phishy as the case may be).
Other types of phishing attacks
Cybersecurity criminals are becoming more sophisticated and advanced all the time, but there are several steps you can take to avoid falling victim to phishing attacks. We recommend that you do the following:
1. Employee training and awareness
Phishing attacks need to be top of mind, with staff being conscious to check emails they receive for suspicious looking links or unexpected instructions. It is a good idea to share examples with the team, so they know what to look out for – it takes practice to pick out the warning signs.
2. Implementing an anti-CEO spoofing email feature
Here at CCT, we offer an anti-CEO spoofing email feature so that the company can be alerted when a high-ranking employees name is being used in an email. Messages can be quarantined for further review to minimise the chances of your company being infiltrated.
3. Keep your browser up-to-date
When browsers learn about any security loopholes, they will apply patches to avoid attackers taking advantage of the weakness. By ensuring that you download and install new updates as soon as they become available, you can keep your computer up-to-date with the latest patches.
4. Have an up-to-date SSL certificate for your website
An SSL certification stands for Secure Sockets Layer. It is a digital certificate that authenticates your website’s identity and provides an encrypted connection between a web server and a web browser. By having an SSL certificate, you keep transactions on your website secure and customer information private and secure.
5. Share this article with your staff
Sometimes the best way for people to learn is to have a couple of examples of what to look out for – just like the ones that we ran through above!
We have some more great tips on privacy awareness and business continuity on the blog, so take a look when you have a moment. And just remember – always be cautious of anything in your inbox that looks a little odd. It is probably a phishing email.

