
With data breaches as the biggest risk to companies in 2022, the survival of your business depends on your cybersecurity knowledge. Are you ready to play?
Question 1 – What is the largest contributor to cyber security breaches worldwide?
Well, IBM recently conducted a study into breaches across customers in over 130 countries and found that ‘human error was a major contributing cause in 95% of all breaches.’ ‘ IBM Cyber Security Intelligence Index Report.
We already knew that human error was the direct cause of 41% of data breaches in Australia in July-Dec 2021. But knowing that it contributes to 95% of ALL breaches is pretty scary.
Question 2 – Who is responsible for cyber security within your business?
The correct answer is d). Everyone within your company needs to work together as a team to protect the prize – your business data. Phishing scams are becoming increasingly sophisticated and with so many people working remotely, the threat surface for possible cyber-attacks is bigger than ever before. It only takes one error to compromise your online security.
Question 3 – What are the most common errors that contribute to data breaches?
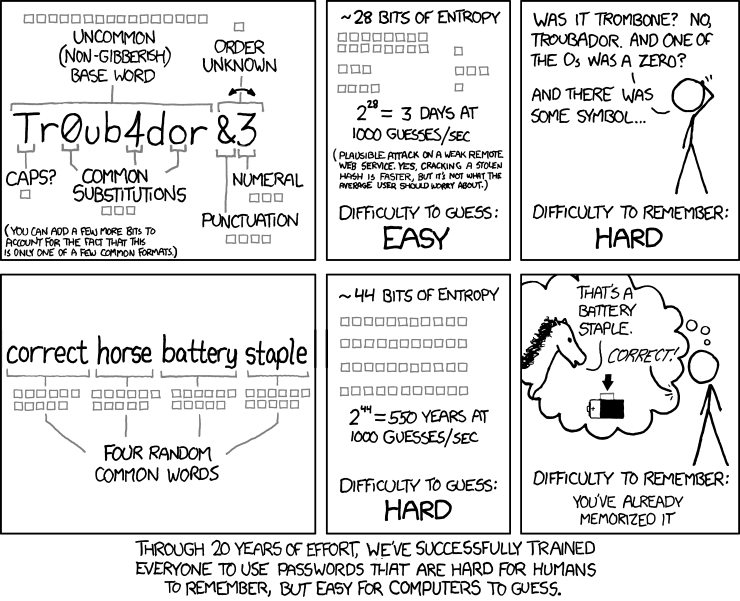
We know that you have too many passwords and you can’t possibly remember them all. But the answer isn’t to use 12345 for all of them and hope for the best. Here is a quick guide to choosing a password that is easy to remember but hard for computers to guess. Plus, you can speak to us about setting up a Lastpass account so that you only have to remember one password at any time.
Do you want to guess how many people still keep their passwords listed on a post-IT note taped to the front of their computer? Unfortunately, the answer is too many. Even if you don’t use the post-IT note method, many people use Google’s password manager. It isn’t terrible but isn’t as secure as you think. Firstly, it doesn’t use a master password to encrypt all of your logins. So, if someone walks past your unlocked computer – they could access all your passwords at once. Secondly, if you sync your passwords across all devices, they can be accessed by someone who hacks into your browser account.
You may have heard of software patches. In simple terms, these are updates that companies release when they discover vulnerabilities in their software that hackers may exploit. If you or your staff regularly click the “Remind me later” button because it seems like too much of a hassle to install an update and restart your computer at that point, then this makes you vulnerable to cyber-attacks.
Another common human error comes from the careless handling of data. We have all probably been in a situation where we have accidentally selected the wrong “John” from our email list. Most of the time, these errors might be harmless, but for sensitive or private data, they can be hugely detrimental to your company’s reputation and your customer’s privacy. One example was the NHS Trust which accidentally sent a group email to nearly 800 patients who had attended HIV clinics in the UK. As a result, they were fined £180,000 for what was seen as a “serious breach of the law.”
Car thieves are going high-tech, scouring carparks with blue tooth scanners to locate cars that have devices in them even if they are hidden out of sight. A 2015 study showed that 45% of healthcare data breaches occur when a USB or laptop with unencrypted sensitive information is stolen. In 2017, a secret service agent had his computer stolen. It contained details of Hilary Clinton’s emails and the Trump Tower floorplans.
Cybercriminals are clever. They target new employees who may not be familiar with the company’s communication methods and “normal” business requests. They leverage current events like changes to interest rates, COVID-19 or increased numbers of parcels posted around Christmas to make their schemes seem realistic. If staff aren’t receiving regular training and education, they may not recognise a phishing scam when they see one. Get in touch with the Colton team on sales@colton.com.au to find out more about our phishing training if you are worried about your staff security awareness.
In case you weren’t sure, the correct answer to question three is “all of the above.” And unfortunately, when it comes to cyber breaches, no one is walking away with a $500,000 prize – except maybe the cybercriminals.
To help raise cyber awareness, we are holding several free cyber security education events in Central NSW in September. Stay tuned for more details over the next few weeks.

