
Did you hear the news? The National Institute of Standards and Technology (NIST) has updated its best practice password guidelines. You might be wondering what the heck that means for you. Well, if you have been following CCT’s advice all this time, not a lot.
The old recommendations
In the past, NIST has recommended complexity (we’ve all seen the “must contain uppercase, lowercase, numbers and special characters” message a million times). Unfortunately, this approach isn’t necessarily foolproof – case in point, Password123!. The old guidelines also had people changing their passwords regularly, often every 60-90 days.
The problem – these recommendations had the unintended effect of users repeating the same password across accounts or resorting to the good ol’ Post-It note stuck to the monitor trick, negating any security benefits.
The new recommendations
The latest NIST update has addressed these issues. To save you from reading the 35,000-word document (linked in case you want to add it to your summer reading list), we have summarised the changes for you here:
What do you need to do?
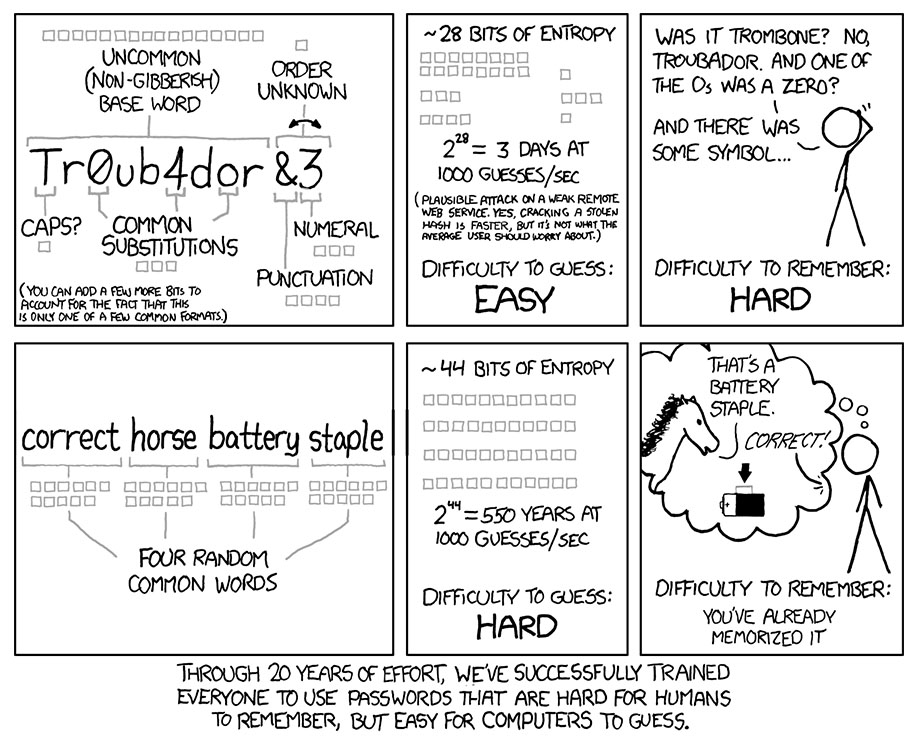
The great news is that Colton has been recommending this best-practice approach for years now. If you sift through the archives, you can check out blog posts like this one from August 2022 and this one from Jan 2023, where we talk about why “correct horse battery staple” is a better password than “Tr0ub4dor&3” and the importance of using a password manager.
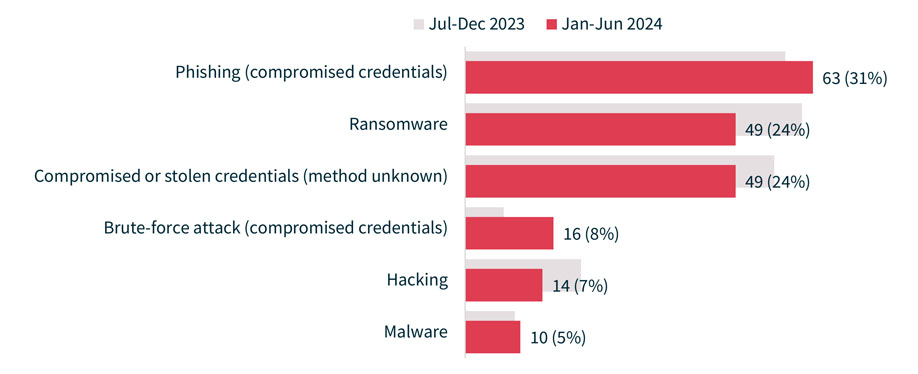
However, it might be a good time to remind your team members about the importance of strong password management. OAIC’s latest Notifiable data breaches report found that 63% of data breaches involved compromised credentials, whether through brute-force attacks, phishing or stolen passwords.
Your responsibility to customers and employees
No matter what industry you are in, you are responsible for taking “reasonable steps” to protect client data, which means protecting against data breaches. The OAIC report listed “addressing the human factor” as one of the critical issues in preventing data breaches, saying that “Entities need to mitigate the potential for individuals to intentionally or inadvertently contribute to the occurrence of data breaches.”
One final recommendation from NIST? ALL organisations should use a secure password manager. So, if your business hasn’t implemented LastPass, now is the time to get onto it.

